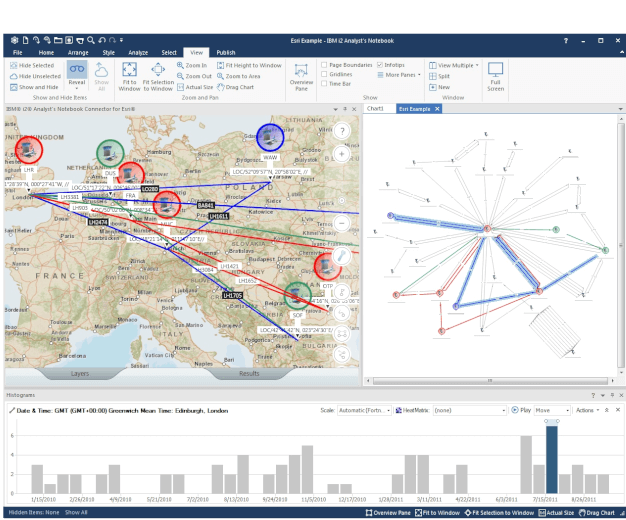
Threats against both public and private enterprise are increasing in number, frequency and sophistication. To thwart these threats, enterprises are faced with overwhelming and disparate data coming from both internal and external sources. They struggle to ingest, fuse and analyze this data at speed and scale to keep pace with rising threats.
Our experienced i2 analysts at Inspire for Solutions Development in Amman, Cairo, Riyadh can detect, disrupt and defeat advanced physical and cyber threats, with the usage of i2 advanced analytics and intelligence analysis capabilities.
Nowadays I2 Analyze is the most trusted intelligence analysis platform for tackling critical missions across national security and defense, law enforcement, fraud, financial crime and cyber.
I2 Analyze Benefits
Complete Visibility
Get a centralized insight into logs, flow and events throughout on-premises, SaaS and IaaS environments.
Eliminate Manual Tasks
Oversee all events related to a particular threat in one place to get rid of manual tracking processes and allow analysts to focus on investigation and response.
Easily Comply
Manage compliance with internal organizational policies and external regulations by using pre-built reports and templates.
i2 Solutions
The most trusted intelligence analysis platform
i2 Analyst’s
Notebook
Arm analysts with multidimensional visual analysis capabilities so they can quickly uncover hidden connections and patterns in data.
i2 Analyst’s Notebook Premium
Combines data storage, analysis tools, visualization and dissemination capabilities in a visual analysis environment.
Security I2 Analyst's Notebook Benefits
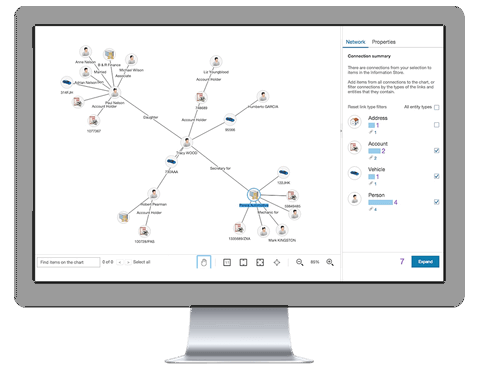
Get Full Intelligence View
Make an analysis of a broad range of data types with a fast data modeling and visualization environment.
Define Key People & Events
Get a deeper understanding of your data with the help of temporal, spatial and statistical analysis views.
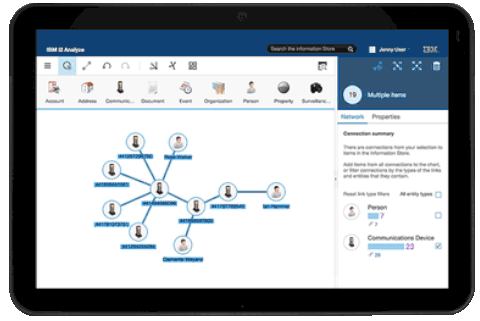
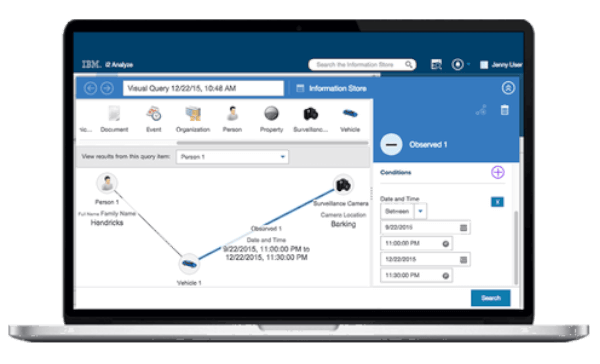
Find Relationships in Networks
Benefit from a clear look on the structure, hierarchy and method of operation of fraudulent networks.
© Copyright 2025 All Rights Reserved
